What is Identity Theft?
When a person is born in the United States, he or she is first meaningfully (and sometimes quite uniquely) named by his or her parents or loved ones, and then inevitably numbered by the Social Security Administration. Ultimately, the number provided by our government is for the purpose of identification and tracking. This sophisticated method of tracking offers perpetrators the opportunity to commit acts of fraud by adopting the unique identifier of another and using that number for nefarious purposes. This is just one example of the growing problem(s) of identity theft and identity fraud. And it is one of the most common (and profitable) fraudulent acts perpetrated by criminals today.
Who is at Risk of Identity Fraud?
Identity theft can happen to anyone. Irrespective of race, nationality, gender, religious views, political affiliation, sexual orientation, or socioeconomic status, its victims can include the elderly and the newborn. It is an equal-opportunity hijacking. Even the mentally ill, infirm, and deceased are not safe. Our information is no longer secure; there is no longer such a thing as “privacy.”
This era of technology allows the digital pillager easy access to an individual’s personal information or a business establishment’s data to open fraudulent credit card accounts, apply for personal or business loans, or access financial records, subsequently allowing a thief the perfect silent opportunity to steal funds from their victims’ accounts. The damage is oftentimes done and the offender has gone long before the victim even realizes something has been taken.
The Role of Digital Science in the Battle
Digital science is extremely helpful in cybercrime. Digital forensics (also known as computer forensics) is a branch of forensic science. It deals with the investigation and recovery of material found on digital devices, often in relation to computer crimes or attacks. Private investigators who specialize in digital forensics can help apprehend the perpetrator by applying investigatory techniques to track activity using specialized techniques and software.

The average person is not privy to many of the programs to which the digital forensic specialist has access; therefore, it is ideal to hire a private investigator who specializes in this field to obtain evidence of fraud. Both civil and criminal matters use digital forensics to help those who have been victimized. Commercial organizations and companies can also use computer forensics to help assist within cases of intellectual property theft, forgeries, employment disputes, bankruptcy investigations, and fraud compliance.
The Consumer Sentinal Network
The Consumer Sentinel Network maintained by the Federal Trade Commission (FTC) tracks consumer fraud and identity theft complaints that have been filed with federal, state, and local law enforcement agencies and private organizations. In 2019, a record 3.2 million fraud and identity theft cases were reported. 1.7 million were fraud-related, approximately 900,000 were other consumer complaints and about 651,000 were identity theft complaints, according to the Insurance Information Institute, referenced in their 2019 Identity Fraud Study.
Warning Signs of Identity Theft
- Withdrawals from your bank account that you do not recognize.
- Not receiving bills and other mail.
- Checks suddenly become refused by merchants.
- Receiving calls from debt collectors regarding debts that do not belong to you.
- Your credit report shows unfamiliar accounts or charges.
- Receiving medical bills for services you did not render.
- Your healthcare provider rejects legitimate medical claims. Benefit limits show to be met, whenever they are in fact not.
- Medical records show that you have a condition that you do not have, of which your health plan refuses to cover.
- Notification by the IRS that you have more than one tax return filed in your name or declares that you work somewhere that you do not work.
- Receiving a notice that your information was compromised by a business that you have an account with or a data breach at an establishment where you do business.
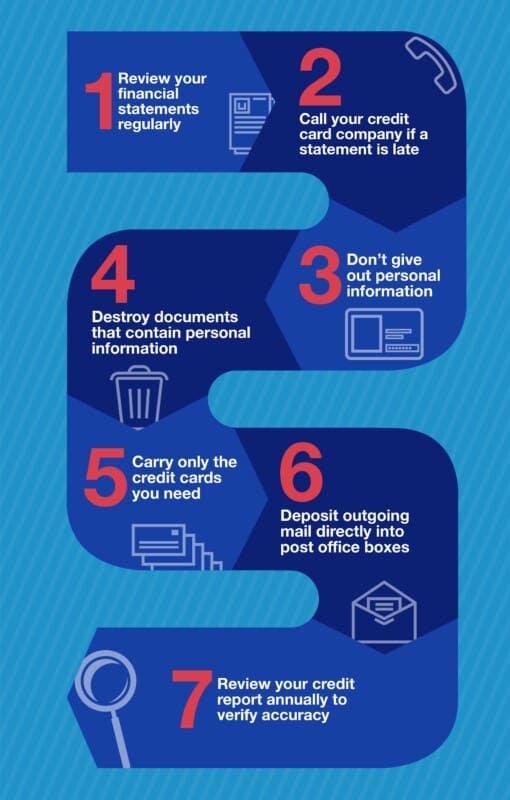
What Steps Can I take to Help Protect Myself Against Identity Theft?
- Protect your Social Security card in a secure, fireproof lockbox. Never carry your Social Security card on your person. Verify the company upon request of Social Security number.
- Do not share personal information with non-verifiable sources. This includes your full legal name, social security number, birth date, or financial institute account numbers.
- Retrieve your mail every day. When you are away from your home or business for an extended amount of time, place a hold on your mail with your local post office.
- Reconcile banking and billing statements from your bank and credit card companies. If financial statements are delayed or don’t reach you, make sure you contact your bank.
- Utilize security features on devices, especially mobile electronics.
- While utilizing public wi-fi, use a private network (VPN), temporarily deactivate sharing capabilities, and update firewall settings.
- Financial institutions such as credit card companies, banks, or credit union statements need to be monitored. Look for unauthorized transactions on statements. Make sure to compare receipts with financial institution statements.
- To prevent “dumpster divers” from accessing personal information shred account/financial statements, credit offers expired credit/bank cards and receipts.
- Install protection software such as firewalls and virus-detection and prevention on all electronic devices.
- Create complex passwords to prevent thieves from guessing them and change them often. If a company that you conduct business with experiences a data breach, change your password immediately.
- Keep your passwords secure and unique. One of the most common sources of information for attackers is the use of a single password for many of your accounts. Apps such as 1Password, Lastpass, and Dashlane can help keep track of your passwords for all of the sites you use in a convenient, self-contained vault. All you have to keep track of is the account password and all. of your site-specific passwords are right there for your convenience. They also have browser extensions that can auto-fill your passwords right into the site so you don’t even have to go searching for it within the app.
- Review your credit reports either annually or semi-annually. Check for unfamiliar accounts. The Federal Government offers one annual credit report from all three reporting agencies at no cost.
- Contact credit bureaus and creditors such as Equifax, Experian, TransUnion, Innovis, National Consumer Telecommunications, and Utilities Exchange to freeze credit files at no cost. Credit freezes prevent thieves from fraudulently applying for and receiving approval for a credit account or utility service in your name.
Where Can I Turn for Identity Theft Help?
The risk of identity theft and fraud exists ubiquitously, especially with regard to digital technology. Still, the same technological advances equally combat this highly personable threat. Therefore, identity theft is both perceptible and largely preventable. One proactive measure is to utilize software services that offer identity theft protection. There are many programs offering identity theft protection to those who wish to increase their security. One popular solution is LifeLock. Another is Identity Guard. Yet another is McAfee (yes, that McAfee, the antivirus guys). For a list of possible solutions, you can also visit Consumers Advocate.

Make sure to perform credit checks frequently. This allows individuals to continuously monitor activity corresponding to one’s social security number. If you have been (or think you have been) a victim of identity theft and need to file a report, please visit the Federal Trade Commission and report your claim. You will have the opportunity to create a personalized recovery plan. The recovery plan consists of a step-by-step recovery process that puts your plan into action, updates your plan as needed, tracks your progress, as well as offers prefilled forms and letters for the advancement of your recovery.
Conclusion
To summarize, individuals and businesses alike need to create an attentive internal system that thoroughly prevents and protects personal, consumer, and business information.
If you suspect that you have been targeted for identity theft or fraud, quickly act by checking credit reports for unauthorized or unfamiliar accounts. If one finds evidence to pursue further investigation, freeze your credit and report the incident to appropriate authorities. Another important safeguard is to employ a digital forensic investigator to trace virtual activity. Ultimately this will be in one’s best interest in helping to minimize the damage and gain evidence if legal action is available.
It never feels good to experience a violation of any sort. Although identity theft is a concerning threat in today’s technological era, taking the steps necessary to protect yourself and your family, as well as your business, employees, and consumers by maintaining a proactive stance can provide one with sound peace of mind.










